Any popular content management system, be it for a blog, a website or a forum, is going to be targetted by hackers at some point. They’ll try to find ways to exploit any security vulnerability that they can find.
To be honest you could expand that statement and simply say “any popular software”.
If the hack is a defacement or similar you’ll notice it pretty quickly, but other types of attack are much more subtle.
Instead of visibly changing a site they’ll take its web traffic.
How?
By intercepting traffic coming from certain sources. So, for example, if you visit the site by typing the address directly into the address bar you won’t notice anything, but if you follow a link from Google or other search engines you get sent somewhere else entirely ie. they intercept search engine visitors.
This kind of compromise has hit pretty much every CMS out there at some point and it’s a hard one to spot unless you take the time to check your web stats regularly. If you notice a sudden dip in traffic then that might be an indicator.
Another way to check, in conjunction with your web stats, is to check Alexa. Yes – Alexa can be useful for something! 🙂
Here’s a screenshot of the stats for a site that was infected by a Vbulletin hack:
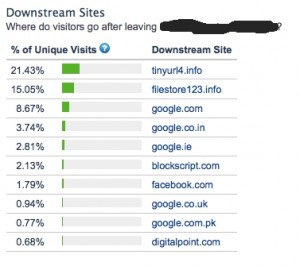 The top two sites are not legit and being used by a number of hacks targeting Vbulletin installs to hijack traffic.
The top two sites are not legit and being used by a number of hacks targeting Vbulletin installs to hijack traffic.
If you’re using Vbulletin there are a couple of tools available that can help detect and remove infections. Vbseo has a good thread on a hack that impacted them and also provide both removal and monitoring tools. There’s also a plugin that will check your vbulletin install for dodgy code. Most of the vbulletin hacks I’ve seen hide themselves in the datastore, so reloading it can remove them, though obviously you need to find the point of entry or it’ll just get reinfected again.
If your site is setup in Google webmaster tools you can keep an eye out for any notifications there. While Google’s tools may not catch all hacks they can spot quite a few and will also do things like informing you of updates to your CMS.
No matter what CMS you are using make sure you keep it up to date AND check for updates for any plugins or extensions you might be using. Remember the TimThumb security issue last year? Thousands of WordPress installs were compromised via a hole in a popular script that was being used by a lot of templates, themes and plugins. Nasty!
Remove plugins and extensions that you aren’t using. Even if they’re not “active” a malicious 3rd party could exploit them.
If you’re running WordPress remove themes that you aren’t using. The defaults ones that ship with WordPress will be kept up to date automatically, along with your core WordPress install, but a lot of 3rd party theme developers don’t provide notifications or automated updates.
If anyone has any other tips or tricks please share them via the comments.







Leave a Reply